Configure a SAML app for Google Workspace
This guide will walk you through the steps to create a SAML Identity Provider (IdP) using Google Workspace to integrate with balenaCloud. At the end of this guide, you can start using Single Sign-On functionality from your IdP in balenaCloud.
Prerequisites
- Access to a Google Workspace admin account capable of creating apps and users for the organization.
Steps
Access the Google Admin Console
- Go to Google Admin Console Apps using your Google Workspace admin account.
Create a New Custom SAML App
- Click on Add app.
- Select Add custom SAML app.
Configure the SAML App
- Name Your App: Provide a meaningful name for the SAML app (e.g., “balenaCloud SSO”).
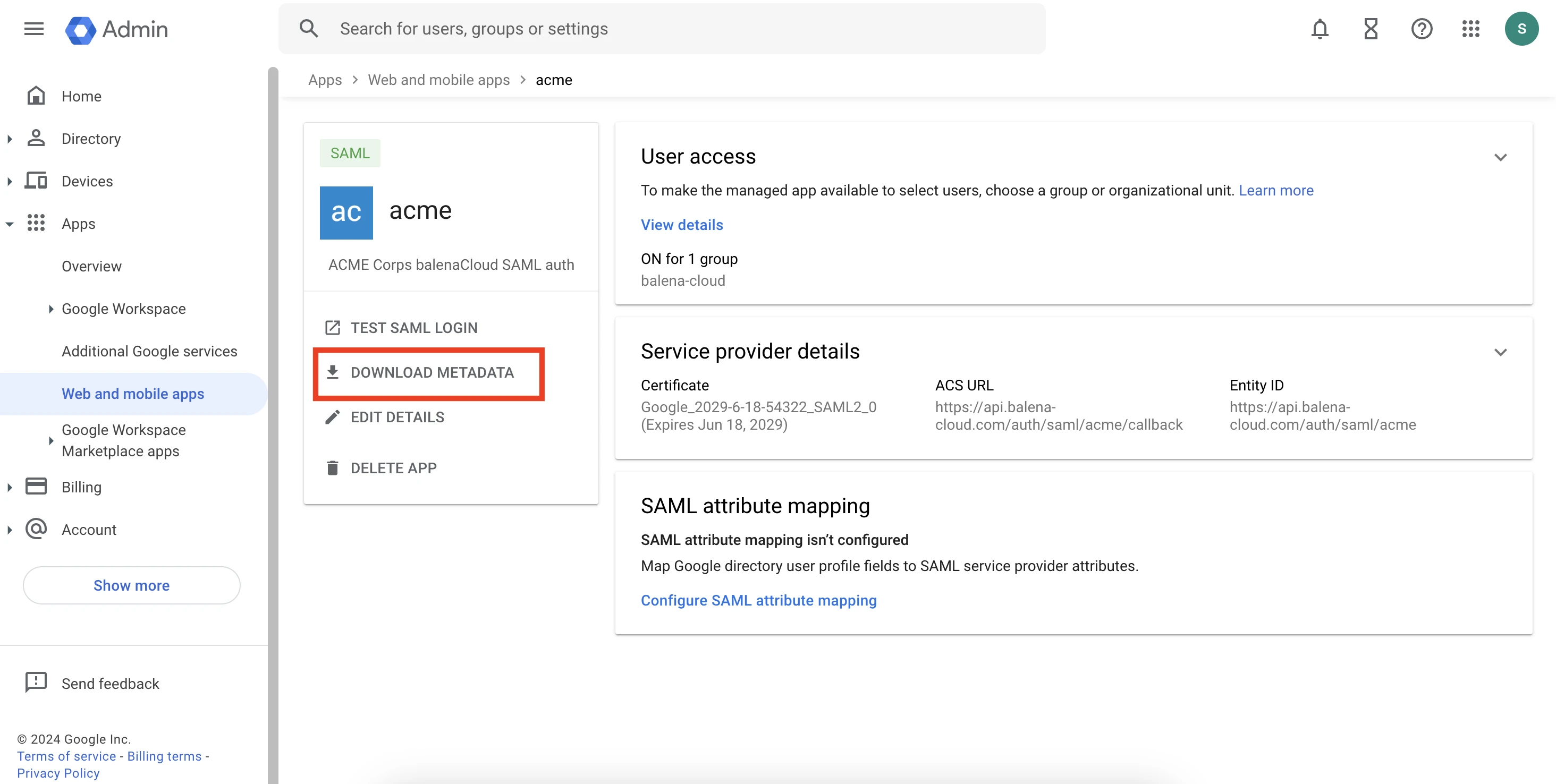
- Download the Metadata: After naming your app, download the metadata file provided by Google. This file will be used later to set up the IdP in balenaCloud.
Set Up Service Provider Details
- ACS URL: Fill in the Assertion Consumer Service (ACS) URL with:
https://api.balena-cloud.com/auth/saml/acme/callbackReplace
acmewith the name you will give your IdP in balenaCloud.- Entity ID: Fill in the Entity ID with:
https://api.balena-cloud.com/auth/saml/acmeAgain, replace
acmewith the name you will give your IdP.Skip Attribute Mapping
- Ignore any mapping configuration. Currently, balenaCloud does not make use of these mappings.
Enable the SAML App
- In the Service Status section, ensure the new SAML app is set to
ONfor everyone or specific groups. This will those users in your organization access to login to balenaCloud via SSO.
- In the Service Status section, ensure the new SAML app is set to
Finally, you should a custom SAML app in your Google Workspace that looks similar to this
Conclusion
Congratulations! You should now have your Identity Provider (IdP) setup, head over to the balenaCloud dashboard and follow the instructions to link an IdP by uploading the XML metadata file. Your team can then start using the Single Sign-On (SSO) functionality, allowing them to securely and seamlessly access the platform using their enterprise credentials.